In the five years that we analyzed the evolution of the Digital Identity Landscape, we’ve found innovation to be a consistent linchpin, a reliable indicator of what the future might hold. In 2020, though, the pandemic’s impact was unprecedented. It forced enterprises, institutions, and governments to transform, prioritizing Digital Identity and placing it squarely in the sights of investors and end-users alike.
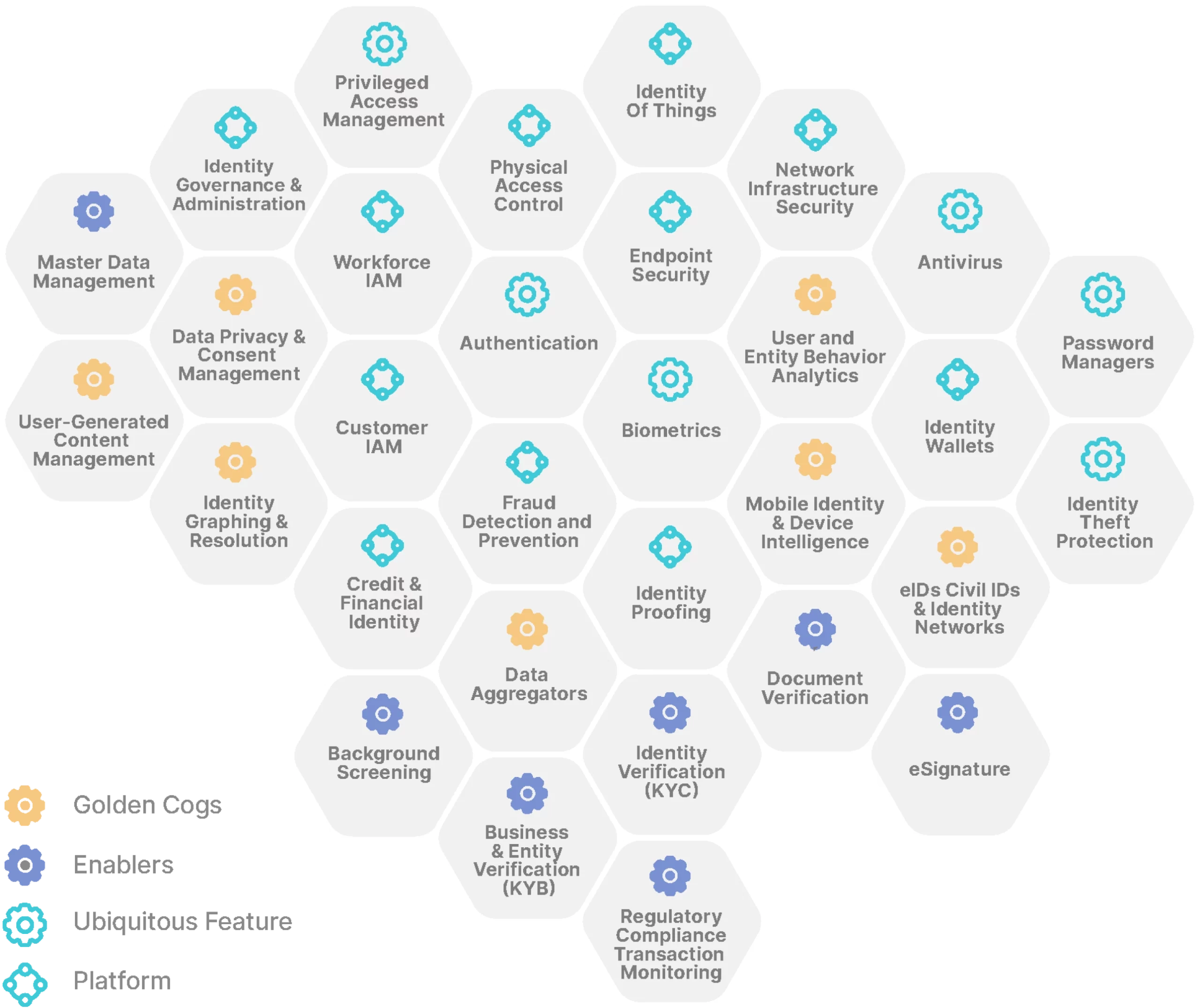
Antivirus
Antivirus software runs in the background and works as a gatekeeper to prevent, detect, and remove viruses and malware that put identity data at risk. Antivirus prevents social engineering techniques, advanced persistent threat (APT), and botnet Distributed Denial-of-Service (DDoS) attacks.
Authentication
Authentication factors are credentials that verify and authorize a user. These are often described as something you know (e.g., a password), something you have (e.g., a security token), or something you are (e.g., a biometric characteristic).
Background Screening
Background screening is the process of looking up and compiling the employment, criminal, commercial, and financial records of an individual or an organization.
Biometrics
Biometrics measure a human’s physical characteristics to verify and authenticate an identity. Biometrics encompass several physiological modalities (e.g., fingerprint, face, iris, palm vein, and voice) and dynamic behavioral modalities (e.g., kinesthetic, device-based).
Business and Entity Verification
Business and entity verification processes ensure that financial services institutions make reasonable efforts to identify and verify the corporate hierarchies, ultimate beneficial owners (UBOs), and ownership structures of the companies with which they do business in order to prevent financial crime.
Credit & Financial Identity
Credit bureaus help companies create a more comprehensive view of their customers to assess credit risk, purchasing behavior, and personal preferences. Alternative credit promotes financial inclusion and the creation of financial identities by using a more comprehensive range of data attributes to determine one’s creditworthiness.
Customer IAM
CIAM solutions focus on identity management for end-users and provide a centralized and managed view of each customer across registration, authentication, authorization, federation, and data capture.
Data Aggregators
Data aggregators gather identity data and attributes from consumers and a variety of independent sources and then repackage or append the data with additional value-add services to enable B2B2C services, products, and experiences.
Data Privacy and Consent Management
Consent management platforms obtain and manage proof-of-consent to collect, share, or sell personal data; they help companies comply with data privacy and protection regulations such as GDPR and CCPA.
Document Verification
Document verification extracts, analyzes, or authenticates different types of global, government-issued identity documents to verify customer information and to establish an individual is who they say they are.
eIDs, Civil IDs, and Identity Networks
Electronic identification (eID) and civil ID schemes are digital identity networks, systems, and credentials issued by governments and other public authorities for proof of identity and to access public and private sector services.
Endpoint Security
Endpoint security solutions protect vulnerable connections across user devices (e.g., laptops, tablets, smartphones, IoT devices) that can compromise corporate network security and the valuable identity data stored.
eSignatures
eSignatures are a digital equivalent of hand signatures and are a legally binding demonstration of consent; solutions may also include electronic certifications, timestamps, electronic stamps, and other proofs of digital authentication.
Fraud Detection and Prevention
Fraud detection and prevention solutions use risk-based approaches to analyze transaction history and network relationship activity in order to identify potentially fraudulent or risky behavior patterns.
Identity Governance and Administration
IGA systems merge identity administration, which addresses account and credentials administration, provisioning, and entitlement management, with identity governance, which addresses the segregation of duties, role management, analytics, and reporting.
Identity Graphing and Resolution
Identity graphs map deterministic and probabilistic data sets to correlate online and offline identifiers with consumer identities. Identity resolution matches disparate records and data attributes to create a single, 360-degree customer view.
Identity Proofing
Identity proofing is a step-up from identity and document verification. It confirms that a user’s identity is associated with a real person, answers the question “are you really who you say you are?” and validates an individual’s identity to facilitate the provision of an entitlement or service.
Identity Theft Protection
Consumer identity theft protection solutions monitor personal data for anomalies (e.g., social security numbers, credit card accounts) and provide paths for identity restoration in the event of theft.
Identity Verification
Identity verification (IDV) often takes place during customer onboarding and combines user-provided and third-party attestations to confirm that a user’s identity is associated with a real person.
Identity Wallets
Identity wallets are smartphone-enabled applications that allow individuals to manage their digital identity credentials and data. Digital identity wallets offer control over what information is shared, when, and with whom, facilitating privacy, security, and consent management.
Identity of Things
IoT security solutions focus on managing device identity credentials, permissions management, endpoint security, and data protection for the billions of internet-connected devices.
Master Data Management
Master data management helps companies maintain a single source of truth for their digital assets, such as customer data. They ensure accuracy, accessibility, and accountability of shared data across the enterprise.
Mobile Identity and Device Intelligence
Mobile identity includes mobile network data (e.g., KYC account information matched to a SIM card) and mobile device intelligence (e.g., location data, biometrics) to detect risk signals, prevent fraud, and improve customer experiences.
Network Infrastructure Security
Network security solutions enable intelligent traffic filtering, performance monitoring, and threat detection to safeguard all data traversing the network and respond to unauthorized network intrusion.
Password Managers
Password managers help customers generate and store secure passwords so that individuals only have to memorize a single, master password. Password managers can also help enterprises set organization-wide password policies.
Physical Access Control
Physical access control manages physical identities and their ability to access the right exits and entries, in the right areas, and at the right time. Applications range from building access to public event safety to border security.
Privileged Access Management
PAM consists of identity strategies and technologies to manage the full lifecycle of elevated (“privileged”) users who have access to highly confidential corporate or government information that can become specific targets for cybercriminals.
Regulatory Compliance Transaction Monitoring
Anti-money laundering compliance solutions and transaction monitoring help financial institutions and money services businesses monitor customer activity and information such as transfers, deposits, and withdrawals to prevent financial crime.
User and Entity Behavior Analytics
UEBA expands upon traditional cybersecurity tools, looks at the behavioral patterns of humans and machines (e.g., routers, servers, endpoints), and applies algorithms to detect anomalies and potential threats.
User-Generated Content Management
UGC moderation is how platforms protect their audiences from illegal and inappropriate content. UGC moderation can identify whether an account is human vs. non-human, providing the ability to remove bad actors before they have a chance to be disruptive.
Workforce IAM
Workforce identity solutions provide full lifecycle management and administration for an organization’s employees, partners, and contractors. Solutions include user registration, authentication, single sign-on (SSO), and access controls.

Ready to get started?
Our identity experts and advisors are available to discuss your requirements, answer questions, and set up a demo of our innovative market intelligence platform.