What Is Digital Identity?
Identity Basics
Managing
Digital Identity
Digital identity is a facet of all our lives now, but confusion exists as to how extensive our digital identities are, and how to go about managing them.
Central role
Digital First
For many sectors of the economy, interaction with customers is now “digital first.” Most relationships with a company or brand are online or mobile, from customer acquisition to online purchases to customer service requests.
This means that, if there is to be any trust in the relationship, it must be established in the digital space. The company or brand must have a clear, unambiguous idea of with whom they are doing business during each and every transaction. For the customer, it means secure transactions, low-friction interactions, and reasonable data privacy measures. For the platform, it means identity verification, authentication, fraud prevention, and so on.
Digital identity systems play a central role in all of this. But best practices for managing digital identities in a robust, systematic, technology-based way are seldom clear. We’ll start by addressing the most common basic questions needed to start managing digital identities in a more mature, intentional way to do just that.
Digital identity is not just information about a ‘digital self.’ It is any attribute about a person, stored and authenticated digitally.
A working definition
What is Digital Identity?
Most simply, a digital identity is information about a person that defines who they are, what they can do, and where they can do it. That information could include traditional “personally identifiable information” (PII) (e.g., name, address, SSN), login data for various sites and online services, online activity, and biometric data or behavioral data.
In short, digital identity is not just information about a “digital self.” It is any attribute about you as a person, stored and authenticated digitally.
For example, suppose a consumer wants to access their bank account through a webpage or mobile app. Consider what is involved:

1
A new online account is created. This would have a username and password associated with it. It would also need to be paired with the customer’s existing bank account, and so…
2
There would be a verification step to ensure that the account holder is the one creating the account. This would link the online account with other aspects of the person’s identity—a government issued ID, an eID, biometric markers (for example, fingerprints), and so on.
3
From there, it is in the bank’s (and the consumer’s!) best interest to authenticate that identity whenever someone tries to gain access. That authentication can be done at several points: At login, when a new device is used, after requesting an irreversible step (e.g. erasing data or sending a message), or when there appears to be suspicious activity.
4
Furthermore, the bank itself would have information about what the account holder could, and could not, access.
All of the information needed to make these things happen is stored by the bank itself and needs to be managed and secured.
Managing digital identity, then, is the set of best practices for implementing digital identity technologies and using them across the digital identity lifecycle. Those digital identities then enable seamless access to other goal-related activities, transactions, and services.
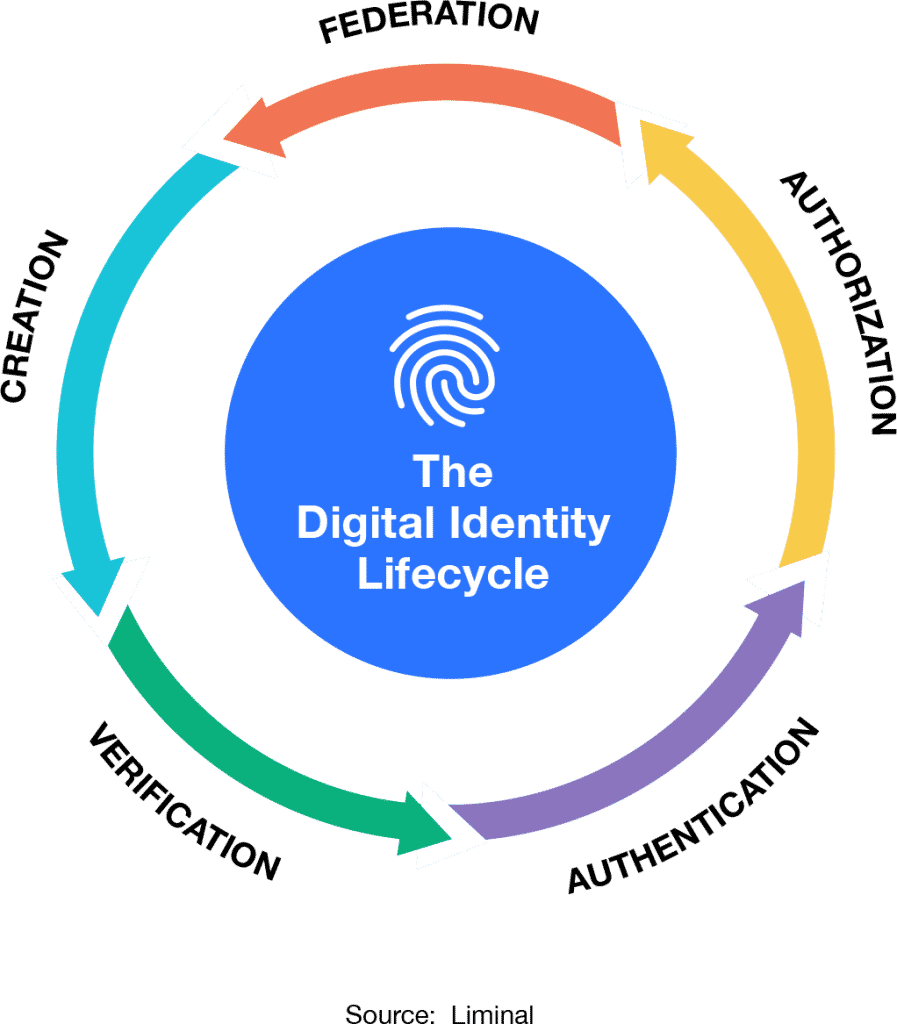
Lifecycle
The Digital Identity Lifecycle
An important aspect of digital identity is that there is a lifecycle to it. Digital identities are, in a sense, “born,” and they grow and mature with use. Less metaphorically: A digital identity is created, then underpins the following steps of verification, authentication, and authorization across various organizations, leading to federation.
Creation
When an operator onboards a user, an account is created and from thereon associated with the user. Usually, that account creation does not require a learning curve by the user or by the organization. But it does require verifying the digital identity of that person, sometimes using third parties or trusted resources.
Verification
Since an organization could not know that the person entering some given credentials was the actual user, early verification through passwords had little value. Furthermore, a newly created identity is of limited value without any verified attributes attached to it. The organization needs a link between the user and something unique to the individual’s identity. This can come in the form of biometrics, a verified ID, or a third-party database, including government sources, social identity, or a user’s phone number.
Multi-Factor Authentication
Now that an identity has been created, and has attributes attached to it, the user needs to re-access this account at a later date. How can we be sure that the previously verified user is now the same user re-accessing their account? When a user attempts to access an account, the organization must ensure that the person has the right credentials and that those credentials have not been shared with someone else. Biometric data, behavioral biometrics, and when and where the person tries to access the site can all help provide this proof. This ensures that the person is who they say they are.
Authorization
Once authenticated, the organization then needs to ensure that the user only accesses the system at the level they have credentials for. Allowing authentication does not necessarily allow full access to a system—bank customers do not have access to the vault simply because they have passed as an authenticated user. Authorization ensures that the credentials are used only at the level of access allowed.
Federation
The less siloed an organization, the better their ability to have a clear view of the user, from onboarding, to client management, to compliance, to customer retention. If every entity within the organization has this clear view and a lack of overlap in the data used, then the organization can hold a stronger view of the customer. Interoperability across organizations and partners also requires consistency in the type of data used to ensure strong identification.
These five components of the identity lifecycle develop an ecosystem of trusted relationships, creating a flywheel for more robust confidence that an individual is who they claim to be. This trusted relationship ecosystem can serve as the foundations for use cases across commerce, travel, banking, education, healthcare, and even democracy.
Components
What Are the Conditions of Digital Identity?
Liminal defines the constituent components of digital identity as different consumer conditions, the most common being data privacy (user information), commercial transactions, reputation, data protection, and inclusion.
Privacy
The consumer’s ability and right to restrict, remove, and protect their digital identity. These are fundamental traits at the core of digital identity wallets and self sovereign identity initiatives.
Commerce
The consumer’s ability to leverage services to initiate online transactions and payments.
Reputation
The consumer’s ability to manage their online presence and information about them. This includes the right to consent to and control data capture, including who has access to your data and understanding why they have access to it.
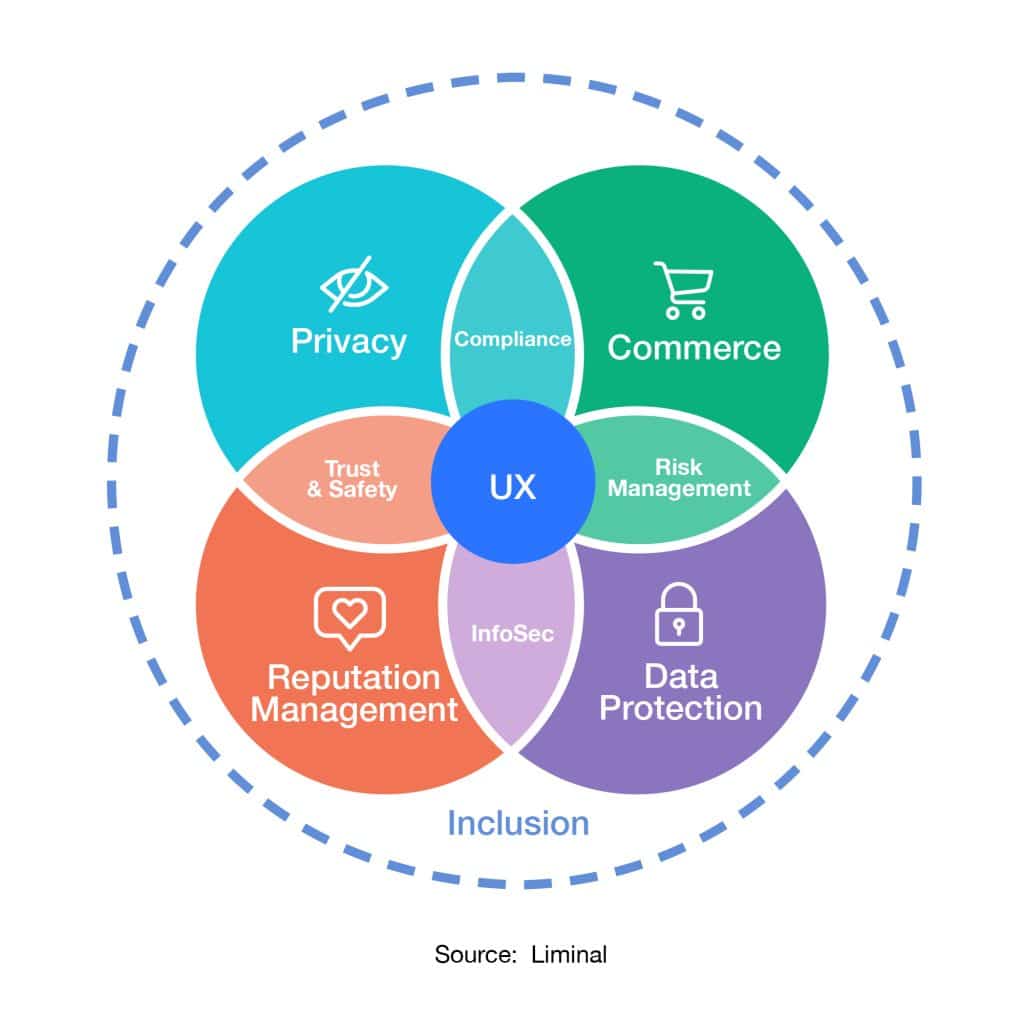
Data Protection
The consumer’s ability and right to protect their data, systems, devices and digital identity from fraudsters,thieves and insider threats.
Inclusion
The consumer’s ability to use services without being excluded due to their personal conditions.
These are important, and consumers are increasingly concerned with all five aspects of digital identity. What has changed in recent years is how these different aspects of digital identity have started to blend together. We are now seeing the rise of Personal Identity Ecosystems (PIEs) as the “connective tissue” between consumers and service providers. There is an evolution here of connected-but-decentralized services; for example, from a one-to-many digital identity wallet, where the user is at the center of the ecosystem, to a many-to-many digital wallet ecosystem.

Digital Identity Management is Fractured
Are Reusable Identities the Future?
Today, consumers individually manage hundreds of online accounts across a spectrum of services and providers.
The challenge for consumer identity management today is that all of this access is being handled by each service or organization individually, in a one-to-one way. Consumers, for their part, are still accustomed to isolated, proprietary solutions and technologies and have been slow to adopt more generalized solutions, such as digital wallets. Conversely, service providers have already sunk time and money into integrating a number of disparate point solutions, and are now loath to write down those sunk costs for an unproven replacement, like a federated digital identity.
And even if service providers were so willing, they still dislike the idea of having their hitherto direct consumer relationships mediated by a third party, especially when data privacy is a concern. As such, users and providers are both unwilling to make the first move in implementing identity federation.The development of reusable digital identities could begin to address existing friction for users and unify the fragmented landscape that they are forced to navigate on their own. Rather than signing up for multiple accounts and verifying their identities with each one, reusable digital identities would help consumers verify their account once. While the concept is straightforward, adoption of the technology to do so is in its nascency today.
The closest thing today would be SSO Google and Facebook, and the interoperability that comes with them. Many online accounts accept user data from those platforms to simplify and streamline the onboarding process for new users. These use cases, however, are largely limited to authentication, with little opportunity for the sharing of verified identity attributes across platforms.
The Other big challenges
Trust, Convenience,
and Fraud
A history of massive data breaches have eroded consumer confidence in large digital platforms. And so, while big tech is in a prime position to capitalize on the opportunity that federated digital identities present, doubts remain about letting such companies continue to own their customer relationships exclusively.
The appreciation for convenience is no less critical, as exemplified by one metric: 42% of consumers abandon an online account due to friction during the onboarding process.
Right now, the PIE space is seeing massive uptick in investments because market pressures are driving innovation.
Finally, the need for better security is facing real downward pressure from fraud and fraud claims. In 2021, the average ticket size for card-not-present (CNP) fraud increased 9.7%. (Source: Liminal Industry Report, February 2022. “The Market Opportunity for Reusable Identity and How to Get There.”)
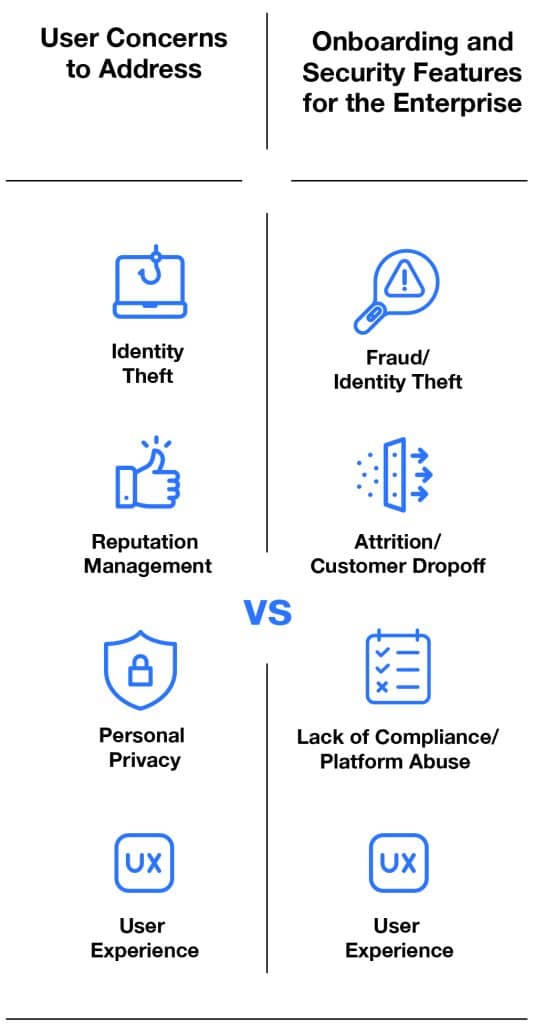
Managing the Digital Identity of Users
Tactical Overview
A full explanation of best practices around managing digital identity is well beyond the scope of a single article. But, at a 10,000 foot view, here are the elements of a digital identity management strategy:
1.
Securing all user groups
There are likely to be differences in managing the digital identities of customers and managing those of employees. Consider all groups that access online assets and what the needs are around those digital identities.
2.
Investing in data security
Beyond identification technologies, organizations should ensure that the data they collect and store is properly secured—for example, through encryption or masking. Access rights to any data should be carefully managed as well.
3.
Taking data privacy seriously
Only collect data that is strictly needed to verify identities and use services online. Be sure to retire data when it is no longer needed (and is beyond the storage requirement for compliance with applicable laws).
4.
Keeping a holistic approach in mind
Forward-looking organizations are already thinking about how they can leverage digital identity more meaningfully, across business units and geographic locations. Managing digital identity will require more than corralling a handful of point solutions and local tactics.
What is the Future of Digital Identity?
Many like to speculate on the future of digital identity, especially because the technology in this area is developing so rapidly. Liminal has established several clear trends going into 2023:
-
Users themselves will begin calling for better security, especially as data breaches become more frequent. They will warm quickly to technologies and processes that can protect their online identity—provided they are educated about their purposes and given a frictionless experience. -
More and more nations will adopt some sort of national digital identity or eID. Some will have the in-house resources to create a working system from the ground up, but many will rely on third-party players who already have proven track records. -
Issues with digital identity will take off exponentially with the growth of the metaverse. Having an avatar or digital double will open up new opportunities for hackers and fraudsters; digital identity technologies will grow in tandem with the metaverse. -
Privacy and trust will be everything. Then again, that has always been the case. Our society is simply at a point when privacy cannot be taken as a given, and trust means actively doing the right things, and not just avoiding doing bad things.
Liminal will take a deeper dive into many of the topics in pieces to come. For a deeper dive on how we begin to assess the digital identity ecosystem, visit Liminal’s Digital Identity Landscape.
